Enterprises face significant challenges in effectively managing vulnerabilities within their systems and networks. The complexity of identifying, prioritising, and remediating vulnerabilities hampers the organisation’s security posture.
Without a streamlined vulnerability management process, enterprises struggle to stay ahead of emerging threats and address critical vulnerabilities in a timely manner. This exposes them to potential cyberattacks, data breaches, and financial losses.
Lack of Visibility
With complex infrastructures and evolution of new threats, it’s difficult to oversee an organisation’s overall vulnerability landscape or stay on top of incomplete or outdated vulnerability scanning methods.
Inefficient Prioritisation
A lack of a standardised framework or criteria for assessing vulnerability severity and the manual or ad-hoc approach to prioritisation increases risk exposure.
Lack of Centralised Approach
Leading to fragmented approaches and difficulties in tracking, prioritising, and monitoring vulnerability remediation efforts.
Inadequate Vulnerability Remediation Processes
Challenges are faced in tracking and managing the remediation progress for identified vulnerabilities with insufficient resources or tools within acceptable timeframes.
Compliance and Regulatory Gaps
Difficulties in aligning vulnerability management practices with regulatory requirements and industry standards are heightened with
incomplete or inaccurate reporting of vulnerabilities to meet compliance obligations.
Integration Challenges:
Difficulties in integrating vulnerability management solutions with existing IT infrastructure, systems, and workflows, impacts the overall efficiency and effectiveness of the vulnerability management process.
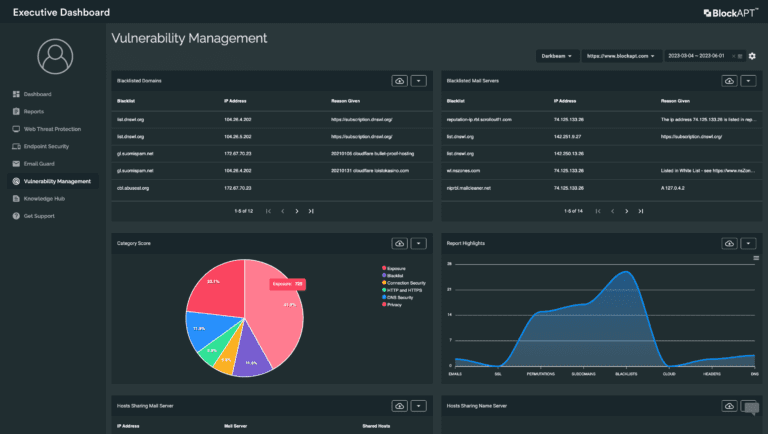
Comprehensive Visibility
The BlockAPT Platform’s centralised and customisable dashboard provides a holistic view of vulnerabilities across systems and networks, ensuring accurate vulnerability detection and reducing blind spots.
Efficient Vulnerability Scanning and Detection
With automated and continuous vulnerability scanning techniques, including network scanning, application scanning, and code analysis, accuracy is improved, and false positives are reduced.
Effective Prioritisation
The BlockAPT Platform utilises advanced risk assessment algorithms and scoring mechanisms to prioritise vulnerabilities based on their severity, potential impact, and relevance with remedial and prioritised actions.
Centralised Vulnerability Management
The centralised BlockAPT Platform consolidates data from multiple sources and provides a unified view of the organisation’s vulnerability landscape. It integrates with existing IT infrastructure, systems, and tools, ensuring seamless data exchange and interoperability.
Compliance and Regulatory Support
Streamline vulnerability management practices with regulatory requirements and compliance processes. Automated vulnerability reporting and audit trails support compliance and facilitate regulatory assessments.
Enhanced Reporting and Communication
The BlockAPT Platform’s executive-level dashboards and visualisation tools makes it easier to communicate insights, status updates, and remediation progress to stakeholders and decision-makers.
Continuous Real Time Monitoring and Reporting
Strengthen defences against cyber threats with real-time alerts, notifications and detailed reports to support compliance audits and strengthen the organisation’s security posture.
Comprehensive and Consolidated Visibility
Have real time comprehensive visibility of up-to-date information about emerging threats and exploits, ensuring accurate vulnerability in a unified view.
Effective Prioritisation of Remedial Tasks
The platform assesses vulnerabilities based on severity, impact, and exploitability, allowing organisations to prioritise remediation efforts and allocate resources efficiently.
Automated Vulnerability Remediation
Leverage the BlockAPT Platform’s automated vulnerability remediation process and reports with recommendations, workflows, and automated actions.
Enhanced Compliance with Security Standards
Streamline and expedite compliance requirements by identifying vulnerabilities that violate security standards or regulatory frameworks in a proactive manner.
Increased Operational Efficiency
The BlockAPT Platform streamlines the vulnerability management process by automating tasks, providing actionable insights, and centralising management. This improves efficiency, reduces manual effort, and allows security teams to focus on critical tasks.