Quantum computing continues to loom over us as an uncertain entity of our near future. We understand the power quantum computing has and its benefits over today’s classical computing. Still, many unanswered questions exist about how it will affect cybersecurity.
The Power of Quantum Computing
With the incredible power of quantum computing comes an overwhelming fear that today’s securities will become obsolete. This fear is very legitimate and should drive security decisions today. Quantum computing has an undeniable advantage in computing the mathematics that current security is based upon. With this advantage, it is speculated that quantum computers can brute force current security best practices at an astonishing rate.
With this said, it is essential to recognise what aspects of current security practices will be affected. No, not all of what we currently use today is in danger; it is primarily the key exchange algorithms. The basis of most encryption is the Advanced Encryption Standard (AES) algorithms. These algorithms are considered to be resistant to the methodologies of quantum.

This is good news as the industry has countless hours involved in its refinement and use. The trouble is that AES encryption requires a key to execute its methodologies. That key must be available to both parties that wish to encrypt and decrypt data. But the key cannot be sent around the internet in plain text, someone would then have the key right along with the encrypted data, and you might as well not have even encrypted it. The safest way to exchange encryption keys would be a physical transference. My colleagues and I refer to this as a “sneaker net” because you get up from your computer and walk, using your sneakers, over to the receiving side of your message and manually enter your encryption key. It is easy to see that this is out of the question in our world of interconnectivity. This is why public key exchange methodologies were created.
These exchange algorithms allow each communicating side to execute an initial handshake establishing public/private key pairings. These key pairings enable each side to encrypt and decrypt messages in a one-way fashion. Party A can encrypt a message with Part B’s public key. The only way to decrypt that message is with Party B’s private key, which hopefully only Party B can access.
While these current key exchanges are based on outstanding and complex math, they are no match for quantum computing. Quantum computers are based on qubits instead of traditional bits. Traditional bits are binary and can only exist as a 1 or a 0. Conversely, qubits can exist in a superposition of 1 and 0. This means a qubit can represent numerous combinations of 1 and 0 simultaneously. So instead of systematically guessing one key at a time like a classical computer, quantum computers can try many keys simultaneously. The results of this operation can then be analysed, all wrong information being swept away, leaving only behind the correct key. This takes time to hack contemporary key exchanges from thousands of years to seconds. It was never that classical computers could not perform the operations to hack the key exchanges; it is merely the fact that the hacks would take far too long to be valuable.
Post-Quantum Cryptography Standardisation Project
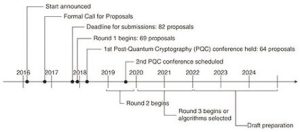
Realising that quantum computing can exponentially speed up the time it takes to compromise public/private key pairings has led to a focus on quantum-resistant key exchanges from the academic mathematics community. In 2016, the National Institute for Standards and Technology (NIST) embarked on the “post-quantum cryptography standardisation project.” The project started with over sixty-five submissions and is currently in the fourth round of review and submittals. The proposals get put through the wringer each round, and even as late as round four, submissions have been deemed insecure. Two algorithms, SIKE and SIDH, which seemed very promising, were found to be insecure by way of a relatively simple hack in August of 2022, 6 years after their original submission. This shows how difficult it is to develop and test these quantum-proof algorithms. The project from NIST is still active, with three other fourth-round submissions being evaluated and one being recommended for standardisation, CRYSTALS-Kyber. This is an extensive process full of significant testing and analysis —still, the pace at which post-quantum standards are set leaves a hole in data protection.
While some argue that this is acceptable because quantum computers are not widely available, I would submit a challenge to this thought. Cybercriminals are very intelligent and some of the cleverest minds around. So, while they might not have a quantum computer at their disposal, they still realise the ability for quantum computing and are preparing for the day they do. Instead of waiting for access to a quantum computer, cybercriminals are capturing large amounts of data today in anticipation. Once access to quantum is available, the criminals hope to decrypt the information they have been storing, gaining tons of sensitive data.
Your Personal Identifiable Information (PII)
You might be thinking, ‘well, that might be years from now, so will that information still be relevant?’ M answer is yes. Here is an anecdote: I opened my checking account in 1996 and have the same account and routing numbers today. Some of the most sensitive and personal information in our lives rarely, if ever, changes. A few commonly accepted Personal Identifiable Information (PII):
- Name
- Address
- Telephone number
- Date of birth
- Passport number
- Fingerprint
- Driver’s license number
- Credit or debit card number
- Social Security number

When was the last time these critical pieces of information changed? Some may happen more often than others, but it is rare. This compellation of data makes you who you are, which means it is used to prove identity. At some point, you must send some or all these pieces of information to different parties during significant life events. No more are the days of only handling consequential matters in person.

Cybercriminals are strategically trying to capture the secure transmissions that include sensitive data in hopes that they can utilise quantum later to expose the data for nefarious acts. This circles back to my original point. Quantum is coming, the battle is here, and you should have some fear. The good news is that some steps can be taken to significantly reduce risk while we wait for standards and regulations that force the use and adoption of better security. This responsibility of increased data protection and prep for quantum falls to enterprises that provide applications used in consumers’ day-to-day lives. It is hard for consumers to take steps independently aside from limiting the data sent, not downloading suspicious items, using VPNs, etc. Consumers must put trust in the mobile and web applications they use for data transference. With that trust comes immense responsibility for the enterprises providing these services, to keep customer data safe.
A Shift in Best Practices & A Focus on the Future
So long are the days of reactive cybersecurity and doing the bare minimum best practices to protect data. Today’s best practices rely on operating systems and communication protocols to orchestrate data protection. While these are essential, application providers are currently washing their hands of security and giving up control. This is why there are an overwhelming amount of zero-day attacks each year, resulting in millions of records being stolen, and this is without quantum computing. There needs to be a paradigm shift in security. Monitoring for breaches and data leakage is too late; the data is already gone. Organisations need to be more proactive in their approach to data protection. The hacks and breaches will never stop, so why not protect the data in a way that anticipates future vulnerabilities and keeps the data secure regardless?
The answer to this problem is quite simple. Incorporate a quantum-resistant application-level security that compliments securities that already exist. The current security strategies and best practices are great at what they do, but we need to do more. Adding a quantum-resistant data security layer to applications will protect data at its source. This contradicts current standards, where data is only secured once it arrives at the communication protocol via TLS orchestrated by the operating system. Data, in turn, is left unsecured as it bounces around before it is sent, promoting a loss of control for the data owners.
This model keeps application providers in constant catch-up, waiting for the next patch to make their data safe again. If instead, applications incorporate quantum-resistant security toolkits that they control, data can be secured without the reliance or intervention of any outside party. Data can be secured as soon as it exists in the application and only unsecured by the endpoint that interprets it. By doing this, the data remains secure regardless of who is in the middle, the operating system or communication protocol version, what malicious programs exist on a device, the network’s security, or how many hops are involved in transporting the data, etc.
This may seem like a tall order, but as mentioned before, the basis of current security methodologies is already quantum resistant. It is only the key exchanges that are thought to be vulnerable. We possess the technology already. Security modules that use these base algorithms uniquely to ensure quantum-level protection exist today. These modules are self-contained, putting control in the hands of the applications, eliminating trust, and introducing redundancy to data security. The time is now for adapting such technologies and shifting the paradigm in data security.
Quantum is coming faster than we think. We see the anticipation spark initiatives for both the positive and the negative. Currently, all our data security eggs are in one basket. From an engineering perspective, this is an astonishingly lousy design. Businesses are proactive and have redundancies in all other facets, so why not in the security of their most significant asset, data? The time to add layers of data security is now, and we don’t have to wait for quantum-proof key exchange to be official from NIST. Application-level quantum-resistant security modules are readily available and should be the primary focus of any enterprise’s security initiatives.








