Since ancient times people have been trying to predict the future and, on issues pertaining to digital, make predictions about technologies. Cinematography in this has long accustomed us in painting despotic scenarios. Many films, in recent years, have provided an apocalyptic vision of the world made up of alien invasions and sick worlds and population crises under oppressive policies. Indeed, dystopia has found fertile ground in cinema and the silver screen by sowing doubts and troubling messages about the future. A dystopia that feeds on characters oppressed by the landscape in which they live made of rigid laws and balances that cannot be shaken. In these scenarios there is no single antagonist; evil is scattered within a sick society that lives in and is subject to certain compromises. Leaving aside this cinematic parenthesis for a moment and returning to those who work in the field of Cybersecurity, prediction is based on elements that are already visible and often already present. Therefore, while for the casual reader, the topic of forecasting on cybersecurity issues may sound like guesswork, for those working in the field it is incumbent to anticipate events proactively, anticipating what cyber crime may be planning. So, let’s try in this article to suggest some trends that we are observing, themes that are still immature in some areas, but which technological speed is bringing to the forefront, and which will soon be coming out of the headlines to become themes that CISOs will have to deal with practically.
Staying in the Cloud
I believe that in this transitional period, when many companies are still evaluating and reviewing their infrastructures, both on-premises and in the cloud, the acceleration in favour of multi-cloud infrastructures will take off rapidly in 2023; the key drivers of this will be competitiveness and flexibility of organisations. Cloud computing will be instrumental in simplifying IT spending, streamlining processes, and finally making that digital transformation run that will be key to generating new business for companies, and greater efficiency in the public administration sector. Let’s also prepare for a lot of buzz on the topic of SASE (Secure Access Service Edge) – a technology that is about to get a major boost in the area inherent to cybersecurity as well. Organsations are increasingly looking for simplified solutions, technology stacks that realise an alignment between performance and security in a scenario where user data becomes diverse, distributed and as far as the security issue is concerned more vulnerable. It is legitimate to think of protected data getting closer and closer to the edge of the network effectively zeroing the minimum distance to the end user. Scenarios that will require a rethinking of security operations and the entire monitoring theme.

Ransomware on the rise and increasingly targeted.
If anyone still does not have a sense of how this scenario has seen an exponential increase in attacks and victims, they can safely do a search on the search engines to see how news regarding this issue is the order of the day and present now in all the major news outlets.
In this context, we have seen increasingly targeted and sophisticated attacks in addition to, the increase in numbers; as reported in various reports, ransomware is increasingly being customised and diversified so as to be effective once launched against a specific technology stack of an organisation. In the crosshairs of these attacks have ended up large organisations, multinational corporations, and services that can hardly afford a prolonged interruption of services. More and more companies, municipalities, public administration, and health care organisations will need to ensure that they are fully protected in addition to verifying the full functionality of backup and Disaster Recovery (DR) processes along with their business continuity procedures. Integrating scenarios that provide for periodic exercises simulating this type of incident and thus testing procedures, people with special attention to the whole topic of communication with the outside world that must be prepared and integrated into the organisation that will deal with incident management and business continuity.

API and 5G
The 5G mobile network is reaching a whole new dimension that can be an accelerated vehicle to many of the existing threats. In addition, automation, and integrations from cloud to app, app to app, ecosystem to ecosystem, and beyond, all imply the presence of different APIs which, for the cybercriminal, means more surface that can be exploited. The design, therefore, of new secure software solutions must move from more security integration in the infrastructure, in the network, all the way down to the application in the stack. Between 5G connectivity, weak IoT cybersecurity standards, and an ever-expanding world of APIs, it won’t be long before flaws, yet unknown, result in high-impact incidents.

Training and cybersecurity
Training continues to be one of the issues to be taken care of and in case, it has not been done, implemented as a regular measure in organisations. Humans have not evolved to detect dangers in the digital world; we are still very much anchored in the physical world and its dangers. Moreover, the education system does not teach how to defend against the dark arts of cyber-attacks. Human risk remains, therefore, an organisational problem. It will therefore be our responsibility to equip our employees with the necessary skills to understand how to counter direct-to-person cyber-attacks such as, for example, phishing attacks. Automation, adaptive learning, and artificial intelligence/machine learning can help provide personalised training on a large scale. Certainly, these technologies will support us in increasing engagement so that people can participate in relevant training that stays at the edge of their skill level to improve and stay engaged. It is proven that a long, dry video followed by a punishment-based phishing simulation does not work. Fixating on failure leads to failure. Rewarding people as they acquire skills in a dynamic learning environment confers measurable improvement. This approach broadly describes gamification, whose proven success is based on established behavioural science and business principles and will be critical to protecting organisations of all sizes for years to come.
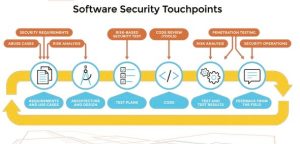
Software security and procurement
Lately, all nations have begun to address the issue of risks and vulnerabilities arising from B2B and B2C technologies created, developed and operated by foreign countries, a recent example being TikTok, a Chinese cloud software. This has begun to raise many questions about where the code and applications come from, what data is put into these applications, and the sovereignty of this data. In 2023, we will begin to see more scrutiny of the provenance of developers and code and more and more organisations focusing on software composition analysis and secure code development. In essence, it is about questioning every component of our nation’s supply chain. Covid has challenged our supply chain in general, and this year we will begin to see more attention to the security risks associated with our supply chain that feeds software development from abroad.

Cyber Insurance
In recent years we have witnessed the death and rebirth of the cyber insurance industry. Cyber insurance companies have experienced cost increases in the areas of ransomware and incident recovery. In response, premiums are beginning to skyrocket, new pre-policy cybersecurity compliance standards will become the industry norm, and conditions, I believe will change. Therefore, rising cyber insurance premiums and stricter requirements to obtain cyber insurance can be expected, which are interesting themes to watch in 2023. On the other hand, we are also likely to see an increase in demand resulting from the growing incidence of supply chain problems. Because of these problems, it is likely that companies will begin to increasingly require that the suppliers or third parties they work with have cyber insurance.

Automation
In this year, we will certainly see automation move into the few remaining areas of security operations that still depend on manual processes. These areas include threat exposure management, which helps to holistically answer questions that want to clarify our ability and preparedness to detect and respond to attacks. Another area that will become increasingly automated is detection engineering, which still depends heavily on specialised skills and tribal knowledge. Automation will not only reduce risk for these organisations, but it will also free SOC staff from mundane tasks so that they can focus on more interesting challenges that really require creativity and human innovation, such as threat hunting and understanding new and novel attack behaviours.
OpenAI, Chat GPT
Chat GPT, or rather Generative Pre-trained Transformer, is an advanced form of AI technology developed by OpenAI. It is a language model that can understand natural language and generate text indistinguishable from human writing. Chat GPT has been trained on a huge amount of data and can produce coherent and grammatically correct sentences. How will ChatGPT revolutionise the cybersecurity industry? Chat GPT has the potential to revolutionise the cybersecurity industry in several areas. For example, we can expect a definite improvement in threat detection, Chat GPT certainly can help improve threat detection capabilities by analysing large volumes of data and identifying potential cyber threats. It can analyse data patterns to identify suspicious behaviour and detect anomalies that could be indicative of an attack. Another area will be incident response, here time is of the essence. Chat GPT can support security teams to respond more quickly to incidents by analysing data in real time and making recommendations for countering them. And ultimately, also in improving decision making.
Watch for economy recession

It is very likely that the recession will cause a reduction in spending, and many of the investments in the bellies of organisations will be revised or will be subject to revising. Despite the idea that cybersecurity may be a recession-proof industry, it is likely that staffing and quality will suffer some setbacks during the economic downturn. There are currently no cuts in basic cybersecurity budgets, but it is likely that more discretionary areas, such as training budgets, or driven innovation may be reduced. When it comes to training, the industry is already facing a skills shortage and, unfortunately, this shortage is likely to worsen as the recession arrives in 2023.









