Cyber insurance
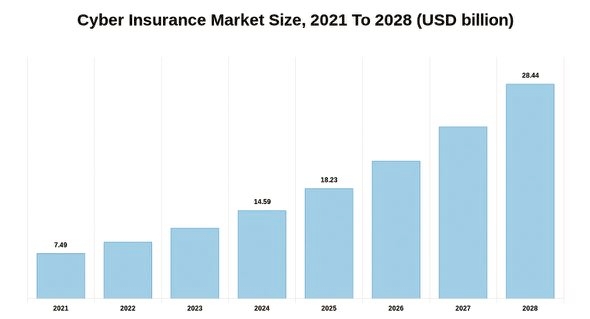
It is estimated that the global cyber insurance market will double in size by 2025, to reach a total market size of approximately 22 billion U.S. dollars. Generally, cyber insurance is designed to protect businesses from risks arising from the use of data and technology in business operations.
During the past few years, cyber insurance has become a hot topic due to rising costs and compliance requirements. Insurers have experienced heavy losses by paying ransoms, which has led to increased costs and stricter security requirements for customers. In 2023, we anticipate that some industries, including healthcare, critical infrastructure, finance, managed service providers, and cybersecurity vendors, will face even more stringent regulations and higher costs from insurers. Some insurers may even require companies to use security solutions from recommended vendors before underwriting their policies. As a result, companies that do not follow cyber recommendations from insurers in targeted verticals should prepare for increased premiums and stricter compliance regulations.
To obtain affordable cyber insurance coverage, businesses must provide evidence of compliance with cybersecurity standards and best practices. They can conduct enterprise risk assessments to determine the maturity level of their cybersecurity program and proactively address underwriting concerns. Risk assessments can guide decisions around insurance gaps, limits, and coverage, and identify acceptable and unacceptable risks to be transferred to insurers.
It is anticipated that cyber insurance premiums will rise, along with the deductibles, while the coverage and pay-outs for claims are expected to decrease. Moreover, recipient eligibility may become more limited, with certain security benchmarks required to be met prior to coverage, which could prove unrealistic for smaller or less well-resourced organisations. Some sectors or types of organisations may also face exclusions from coverage, along with certain types of cyberattacks. In response to these changes, more companies may emerge as ransomware «brokers,» acting on behalf of victims to negotiate ransom payments. This trend could result in an increasing number of organisations seeking assistance from such brokers during times of need.
Ransomware
Gartner predicts# that nation-states are likely to enact legislation about ransomware payments. In 2021, Gartner estimated that less than 1% of global governments have rules around ransomware but forecasts that figure will grow to 30% by 2025.

In 2023, cybercriminals will target data since it can be used for many purposes, such as ransom, identity theft, and targeted advertising. Breaches of Windows and Linux machines will be a critical data threat, and database breaches will continue. Ransomware will be a major vector for data theft and may be used to blackmail enterprises by threatening to expose data breaches publicly. Ransomware groups will adopt different operational models and new attacks, such as cloud-aware ransomware, as more businesses store their critical data in the cloud. Cybercriminals react to security strategies from law enforcement, governments, and private industries, such as cloud adoption and hardening networks.
All you need to do to get the pulse of the ransomware threat today is pull it up as a search term in the news on any given day of the week. Ransomware attacks happen in one of two ways: by opportunistic means, or by targeting someone or something. Targeted attacks are way more sophisticated and specific, and we have seen an increase in reports that indicate custom ransomware has been launched against an organisation’s specific technology stack. In the crosshairs have been large organisations that are multinational, and throughthe definition of its services cannot endure a prolonged outage. More companies, more municipalities, and more core service businesses must be on the lookout, and ensure they are comprehensively protected by a triad of methods: secure the environment, have a plan to elegantly recover from a breach, and an ongoing assurance plan of security and compliance.

Ransomware is a destructive tool that cybercriminals frequently use. According to US security agencies, the Hive ransomware has extorted about $100m from companies since June 2021.
Miri Marciano, a cybersecurity expert, indicates that ransomware is increasingly dangerous due to its double extortion tactics, ransomware as a service and massive DDOS attacks. As a result, businesses are forced to seek managed security services providers to cope with the high competition for cybersecurity experts. To eliminate ransomware, Adam Brady, director of systems engineering for Illumio’s EMEA operations, believes that governments and the industry must work together and eliminate the payment of ransomware. While new legislation is unlikely in the next year, discussions may arise about how to address ransomware.
Remote work
Research suggests that the chances of data breaches occurring are higher when employees work remotely. This could be due to factors such as less secure home networks, increased reliance on personal devices, and potential lapses in adherence to security protocols.
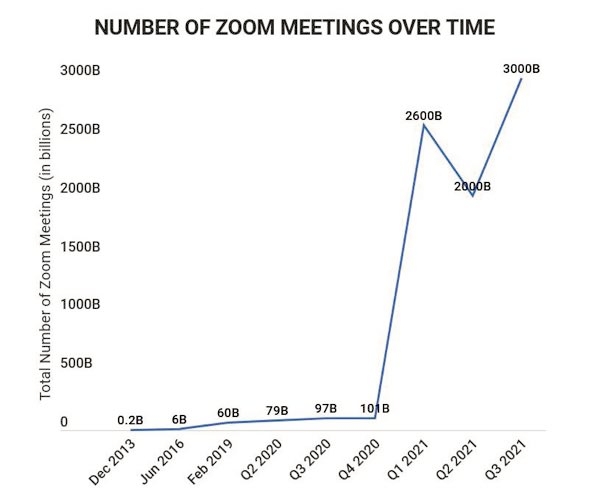
According to Zoom’s user statistics, the platform experienced substantial growth throughout the COVID-19 pandemic. As of 2021, the number of daily active users surpassed 300 million, representing a staggering increase of 2,900%.
The pandemic caused many companies to shift to remote work in 2020, resulting in new vulnerabilities for businesses. Hybrid models of working will further alter traditional security architecture and expand the attack surface, says Kelly Ahuja, CEO of Versa Networks. The security technologist of VMware, Chad Skipper, warns of “island hopping” in 2023, where a threat actor hijacks an organisation’s infrastructure to attack its customers. Remote desktop protocol is a top threat and must be a priority for all organisations, particularly in healthcare given the sensitive nature of personal health data and the regulations across the sector.

Many employees are now familiar with hybrid work, switching between working from home and the office. This means work devices move between secure and unsecured zones, making security a challenge. Enterprises will adopt zero trust models to combat these security issues. However, we anticipate that threat actors will increasingly target home devices connected to enterprise resources, with attackers pivoting into home networks connected via VPN to move laterally into the enterprise network. This tactic allows attackers to compromise the current network and potentially target multiple networks in the future.
Zero Trust
PWC’s 2023 Global Digital Trust Insights Report reveals that over a third of CISOs (36%) have already initiated the deployment of elements related to zero trust, while an additional 25% plan to do so within the next two years.

Many sources cite that the industry is still under utilising Zero Trust cybersecurity principles. Updated security platforms and tools are broadly adopting Zero Trust integration and for the most part, this appears to be a cultural and educational matter that will see increasing adoption in the year ahead. While Zero Trust is not the proverbial ‘silver bullet’ of cybersecurity, it is part of the foundation of evolving cybersecurity that strives to authenticate users everywhere possible in a modern cloud infrastructure.
Remote work is expected to continue, and VPNs may not be able to keep up with scalability demands and cybersecurity threats. The “zero trust” approach provides both scalability and high security by continuously validating and re-evaluating users. The Biden administration has mandated federal agencies to implement zero-trust architecture (ZTA) by 2024. Zerotrust network access (ZTNA) is projected to grow 31% in 2023, replacing VPNs entirely by 2025, according to Gartner.
Artificial Intelligence
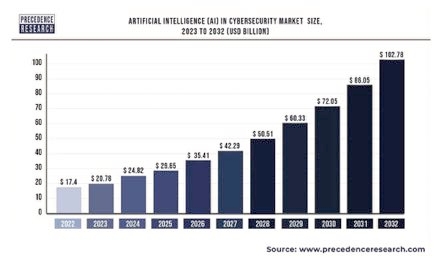
In 2023, the cybersecurity artificial intelligence market will have a value of USD 22.4 billion, and it is projected to reach USD 60.6 billion by 2028, with a Compound Annual Growth Rate (CAGR) of 21.9%.
Tech companies, such as Cruise, Baidu, and Waymo, are testing self-driving cars, or robotaxis, in many cities worldwide, with claims of successful trips for delighted passengers. The appeal for businesses is cost savings from eliminating gig economy workers. However, there have been accidents, and hacking is a concern since internet-connected cars are vulnerable to attack, and humans can engineer AI. In 2023, it’s possible security researchers or grey hat hackers could play a technical prank that causes a robotaxi to become stuck, potentially disrupting traffic. While we do not anticipate dangerous accidents, we expect at least one cybersecurity incident involving these new autonomous vehicles.
AI technology has rapidly advanced in recent years and while it has the potential to benefit various industries, it also presents new risks, particularly in cybersecurity. Miri Marciano, a cybersecurity expert, predicts that AI and machine learning will make social engineering-based attacks more effective by making it easier to collect data on businesses and employees. However, AI-powered cybersecurity systems like SIEM capabilities could be used to detect and respond to threats more efficiently. Meanwhile, there are growing concerns about deep fakes, which use AI to create fake images and videos of real people, being used for impersonation and social engineering attacks. David Mahdi, the CSO and CISO advisor to Sectigo, advises individuals to monitor their accounts regularly and choose biometric authentication methods carefully.
- Cybercriminals will leverage AI and machine learning to strengthen social engineering-based attacks, making it simpler and faster to gather data on businesses and employees.
- AI-powered cybersecurity systems like security information and event management (SIEM) will enable security teams to detect and respond to threats faster.
- Deepfakes, which use AI to create fake images and videos of real people, are likely to be used by cyber attackers for more social engineering attacks and impersonation. This could make biometric authentication methods less useful, and individuals should monitor their accounts regularly for financial services.
- Adversarial attacks against AI systems will become more prevalent as attackers seek to manipulate or evade detection by the system. This could impact the security and reliability of AI-powered systems, such as autonomous vehicles or medical equipment.
- The use of AI in phishing attacks will increase, with attackers using machine learning to create more convincing and targeted emails. This could lead to higher success rates for phishing attacks and more data breaches.
- AI-generated fake news will become more widespread, potentially impacting elections or financial markets. This could lead to significant social and economic disruption and highlight the need for better detection and prevention methods.
- The use of AI to automate attacks, such as through the use of autonomous malware or botnets, will increase. This could lead to a more significant and rapid spread of malware and more sophisticated attacks.
Cloud Expansion
According to Check Point Research (CPR), there has been a 48 percent rise in cloud-based cyber attacks in 2022 compared to the previous year, likely resulting from the heightened adoption of digital transformation initiatives leading organisations to shift their operations to the cloud.

Over the past three years, businesses have rapidly shifted to the cloud and adopted new cloud technology, which has been integrated into the hybrid work environment. However, the biggest challenge facing enterprises is inconsistency across cloud applications due to varying abilities, features, and cost structures of different cloud vendors. This inconsistency could lead to security issues, particularly since many CISOs may not be familiar with new technologies or lack the bandwidth to oversee all cloud vendors. Misconfigurations from users and developers may also arise, as cloud developers may prioritise agility over security. One area of concern is the potential security threats of cloud APIs on connected cars, which are new and complex systems with multiple vendors providing different components. As a result, it may be increasingly difficult to guarantee security for each of these vendors.
In 2023, it is expected that multi-cloud data infrastructure adoption will become the standard as organisations evaluate their current infrastructure, including both on-premises and cloud-based systems. To remain competitive, flexible, and secure, organisations will aim to transform cloud computing into a uniform capability, reducing the overhead and integration complexities of managing cloud services and supporting applications. Security will be a critical concern, particularly when it comes to managing data and configuration in different cloud environments and ensuring unnecessary exposure is minimised through proper control mechanisms.
MFA
In 2023, threat actors will target multi-factor authentication (MFA) users through new vulnerabilities and bypass techniques, relying heavily on social engineering. Increased adoption of MFA, currently at 40%, will require attackers to find ways around these security solutions to succeed. Attackers may use push bombing and AitM techniques that capture authentication session tokens to bypass MFA. Expect many more MFAtargeted social engineering attacks next year.
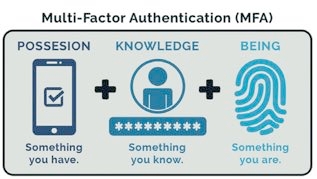
MFA is a security practice used by sectors like online banking and social media to enhance cybersecurity. But, hackers have exploited technical and human vulnerabilities in MFA systems. More organisations adding MFA layers has led to “MFA fatigue” among users, and attackers exploit this to overwhelm employees with approval requests. Notification fatigue was used in several high-profile attacks last year, including the Uber data breach. Miles Hutchinson, CISO of Jumio, predicts businesses will seek alternative verification methods, such as passwordless authentication, to avoid MFA fatigue.
Supply chain
Supply chain attacks grew four-fold in 2021 as hackers targeted smaller organisations in the supply chain with weaker defences. Gartner forecasts a three-fold increase in software supply chain attacks by 2025, with 45% of organisations expected to experience such incidents. CEOs and boards are pushing for security enhancements in their supply chains, leading to greater demand for solutions and services that can catalogue and monitor cyber risks in third-party vendors and suppliers.
Due to the interconnected nature of tech businesses, supply chain attacks are becoming increasingly common and disruptive. Organisations need to consider the security of external companies they work with, as exemplified by the 2020 breach of Solarwinds, which served as a “wake-up call” for companies, according to Zoom’s head of security assurance, Sandra McLeod. Cybersecurity experts warn that in 2023, supply chain attacks pose a massive risk, with attackers becoming faster at exploiting vulnerabilities. To prepare for future risks, proving cyber resilience is crucial, says Kev Breen, cyberthreat research director with Immersive Labs. In response to the wave of supply chain attacks that affected several organisations on its site, GitHub launched a new strategy to enhance the security of open-source projects last October.
Quantum Security
Quantum computers are becoming a reality. They will enable great technology innovations in the future, but equally will bring significant risk in many fields, especially in cyber security. The World Economic Forum (WEF) has identified quantum computers as a significant threat to cybersecurity worldwide. As quantum computers become more and more powerful, the direct threat they pose to current encryption systems is real.
In 2023, organisations will increasingly acknowledge the risks posed by quantum computers and will plan accordingly in order to mitigate that threat. Organisations will start to plan ahead and have deeper understanding in ways in which quantum computers can challenge the integrity of digital documents, break current encryptions, and tamper with sensitive data such as health and financial personal data.
The nature of the quantum threat is such that it cannot be left to the last minute. Organisations must plan years ahead, given that the protocols that we rely on the internet for day to day transactions such as online banking, secure messaging, virtual private networks, etc. are at risk. Switching to quantum secure systems will take years to plan and to implement. For that reason, preparation is key.
The United States has already started the preparation process by initiating the Quantum Computing Cybersecurity Preparedness Act. This legislation reenforces that the quantum threat is real and must be taken seriously by organisations today.
Useful Links:
https://www.forbes.com/sites/forbestechcouncil/2023/01/02/sixcybersecurity- trends-you-can-expect-in-2023/?sh=384e60f24c97
https://www.trendmicro.com/vinfo/us/security/research-and-analysis/ predictions/2023
https://www.watchguard.com/wgrd-resource-center/cyber-securitypredictions
https://www.cisecurity.org/insights/blog/our-experts-top-cybersecuritypredictions- for-2023
https://www.siliconrepublic.com/enterprise/cybersecurity-predictions-techtrends- 2023
https://www.forbes.com/sites/emilsayegh/2022/12/15/top-cybersecuritypredictions- 2023/?sh=75b04322383f
https://www.weforum.org/agenda/2022/09/organizations-protectquantum- computing-threat-cybersecurity/
https://thequantuminsider.com/2022/12/15/quantum-computingcybersecurity- preparedness-act-passes-senate-awaits-presidents-signature/








